Automatic IIS redirect http to https on Windows Server 2016
Because IT-Security IS important
IT security is a big issue today. In order to ensure a good feeling for website visitors, it is recommended to encrypt your websites. Especially when the customer data (user name, password, personal data …) are entered on the website, encryption is compulsory to meet the data protection requirements. This article explains how all IIS requests can be encrypted.
Step-by-step instructions for the IIS redirect http to https
Prerequisites
It is assumed that a server has already been set up with Microsoft Windows Server 2016 and the current IIS 10, so that the web page in question can be accessed on both http and https.
If this does not already exist, the following articles will help:
– How to install IIS 10 on Windows Server 2016 (German only)
– How to get a free SSL-certificate from Let’s Encrypt for IIS Websites (German only)
Preparing your server
Before we can start configuring you server, another tool needs to be installed: URL Rewrite. It is an official extension to IIS and has been installed together with Server Manager up to version 9. From version 10 onwards, URL rewrite must be installed manually. Microsoft’s free EXE should be downloaded, which can be found here: LINK
Building a server configuration
After the installation, the web page’s root directory has to be accessed. The IIS Manager should not be open during this time. The web.config file is required. If it does not exist yet, it needs to be created again.
Once created, open it with a text editor to insert the following text:
Copy<?xml version="1.0" encoding="UTF-8"?> <configuration> <system.webServer> <rewrite> <rules> <rule name="Redirect to HTTPS" enabled="false" stopProcessing="true"> <match url="(.*)" /> <conditions><add input="{HTTPS}" pattern="^OFF$" /> </conditions> <action type="Redirect" url="https://{HTTP_HOST}/{R:1}" redirectType="SeeOther" /> </rule> </rules> </rewrite> </system.webServer> </configuration>
Now the document can be saved and we can open the IIS. Here you have to navigate to the website in question and open URL rewrite. The rule, which has just been created, should appear. This looks (approximately) like the following:
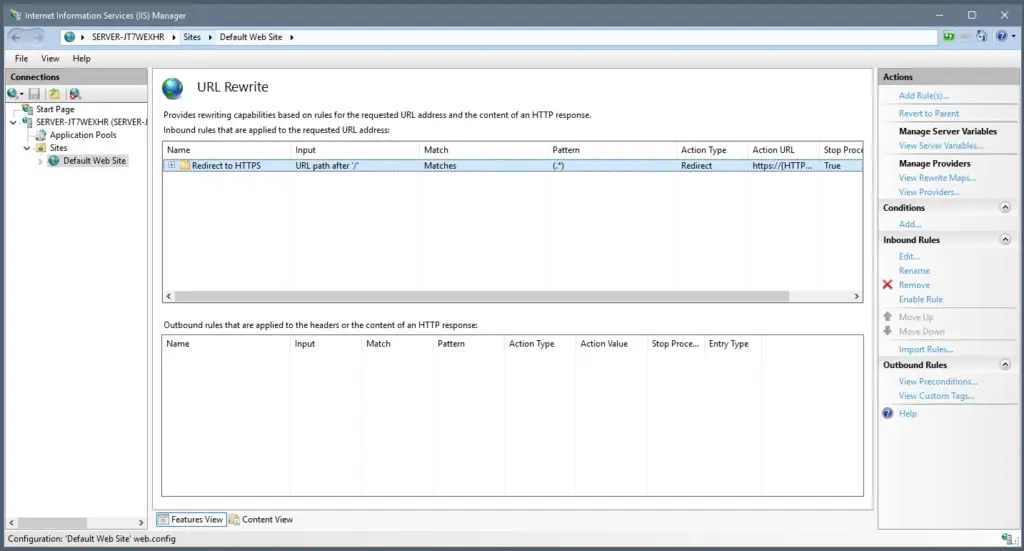
However, the rule is still deactivated. To activate it, find the menu item Enable Rule and click on it.
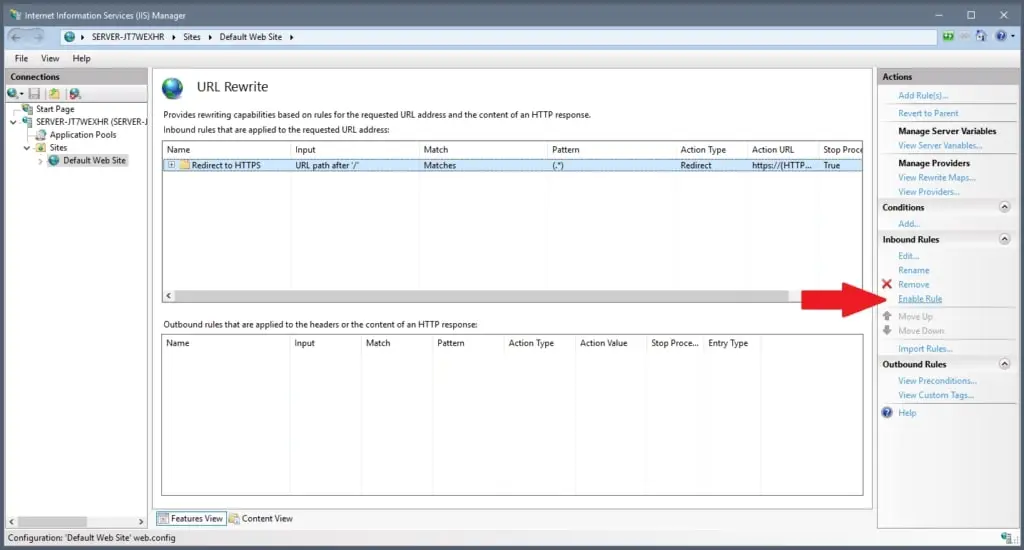
Finished! Http requests are now forwarded automatically to https. Best practice is to test it immediately by opening the website in any browser.
Summary
With little effort, the entire websites traffic is encrypted. Other services, such as WebDAV, can be encrypted with the same certificate too.